Extras din referat
1.Introduction
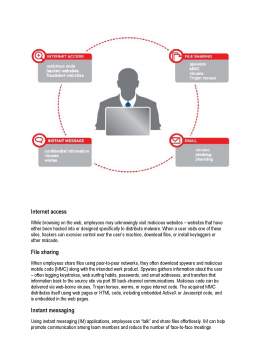
The internet has become a critical resource employees rely on to get their jobs done. Employees use the web to perform research and gather information. They use email and popular instant messaging tools to help them stay in touch with coworkers and customers. And uploading, downloading, and sharing document files and other work products are now everyday activities.
Unfortunately, when employees perform these daily tasks, they expose the companies for which they work to serious security risks. Employers must now be concerned with more than simply preventing employees from doing things on the job that they should not be doing – visiting restricted or inappropriate websites, for example. Now employees are being exposed to harmful, destructive threats while in the process of simply doing their jobs. Companies should examine their IT security measures and determine whether they are sufficient to protect against these web-borne threats.
2. Exposure to Threats
First, let us take a quick look at the overall threat. The original protocols and systems that made up the
Internet were designed to run on an open network. That network was resilient against the threats of
backhoes and nuclear warheads, but not designed to keep out an attacker. Over the last decade, the
attackers have transformed. Originally, the attackers were people who were interested in bragging to
their friends about their conquests. Now, the attackers include criminal enterprises, like the infamous Russian Business Network, who are interested in making a profit. While there are plenty of
opportunists – affectionately referred to as “script kiddies” ‐ who must use tools created by others,
there now are violent organized crime groups who are combining the anonymity the Internet provides
with the difficulty of prosecuting international crimes to create a unique money making opportunity.
One estimate is that there are billions in potential profits from being able to control other peoples
systems: then exploiting those systems or the information on them.The classic method of attackers is to scan the Internet for vulnerable systems and then attempt to compromise them. Now attackers have a complimentary attack vector. Why should an attacker go out and look for vulnerable hosts when the hosts can come to the attacker? An attacker can place exploits on the Internet and attract people to them using Spam, buying advertisements on web pages, and other methods. This way the computers come to the attacker without interference from firewalls or network scanning.
Increasing sophistication of malware
Malware is a term with many different definitions and names like spyware, viruses, adware, trojans, etc.
I use it here as an all‐encompassing term for software that may spy on you, allow others to control your
computer, display advertisements or perform any number of other activities that fall into the category
of your computers working for others. As with most software, the original incarnations were relatively
simple programs compared to today. Early malware (viruses) would attempt to replicate itself and was
occasionally destructive. The authors of this software may have written them as pranks or as a way to
gain notoriety among their fellow virus writers. As more and more computers arrived on the Internet,
especially those with high‐speed connections, people began to notice that the same old crimes committed in the real world could also be perpetrated online. Over time, the attacks have become
much more sophisticated in nature. For example, recent malware usually actively attempts to protect
itself from being removed. Early simple tricks included multiple processes that would restart one
another if one died and stopping antivirus services. Today’s malware can subvert your computer in
ways that make it nearly impossible to remove without reinstalling the operating system. Some
malware authors have even adopted reusable code to aid in quicker development. They also use tiered
applications to both distribute the load of spreading their creations and to provide redundancy so that
when incident handlers do manage to shut down a website, their networks can continue to operate.
Many organizations cannot replicate these skills with their own internal development efforts!
Obviously, something has changed to bring all of this worldwide talent into developing this complicated
software. As you already know, one of the single greatest motivators is money.
Profit motivation of attackers
Both the con artist and criminal organizations have adapted to the Internet. The pyramid scheme, getrich‐quick scams, and extortion have online counterparts and the bad guys seem to be dreaming up new schemes all of the time. As an organization, you could be subject to a distributed denial of service attack against your website in an attempt to extort money from you, directly, or to cause your customers to go somewhere else. Your employees could be subject to identity theft by using an infected computer or visiting websites that steal passwords from web browsers. The “crown jewels” of your company may
even be under attack. If you have a product or a process that other people want, you are going to be
attacked. The FBI has been telling anyone who will listen through its Counter Intelligence Domain
program that foreign intelligence agents are actively attempting to get at your intellectual property.
You may not just be subjected to commercial espionage either. There is considerable evidence that
foreign governments have already probed U.S. government agencies and contractors for weaknesses. If you have something they are interested in stealing, you could be next. Just search for the codeword
Titan Rain, to see the types of directed attacks that were happening a few years ago. The attacks today
are likely even more subtle such as the subversion of certain Greek cell phone switches during the run
up to the Athens Olympics.Certain Chinese IP addresses have been implicated in recent attacks against companies in the UK, the German government and the US Department of Defense. You can be certain that other people are doing their own cost/benefit analysis and figuring out it is much cheaper to hijack your intellectual property than it is to recreate it.
Detailed attack methods
In the following sections, I will cover some of the most prevalent and recent attack vectors. By the end
of the analysis, you should be able to evaluate how capable your controls are at preventing or detecting
these classes of attacks and determine if improvements in your defenses are necessary. Since the
threats are always changing, you should periodically assess your controls in this fashion, or they will
become increasingly less effective over time.
Preview document
Conținut arhivă zip
- Internet Specific Threats
- Internet specific threats.doc
- Internet specific threats.pps